MAP Drives (Q: Drive):
Click on "Go" in menu bar
Select "Connect to Server…"
Enter path: smb://GTCFS02
Click the + button on bottom left (it will be added to “Favorite Servers:”
Click to highlight the address; then click “Connect”
Enter Credentials…(it is not BOOMI)
MACBook Notes
Install Outline from Mac App Store
Locked Print Release Procedure:
*When setting-up a new Ricoh printer, please make sure to download the most current driver for that printer from Ricoh's website…then install the printer (via IP Address) and use the downloaded driver.*
Setup (or access current) user in printer address book by logging in to the printer web page…
Add printer to users computer via print server or direct IP…
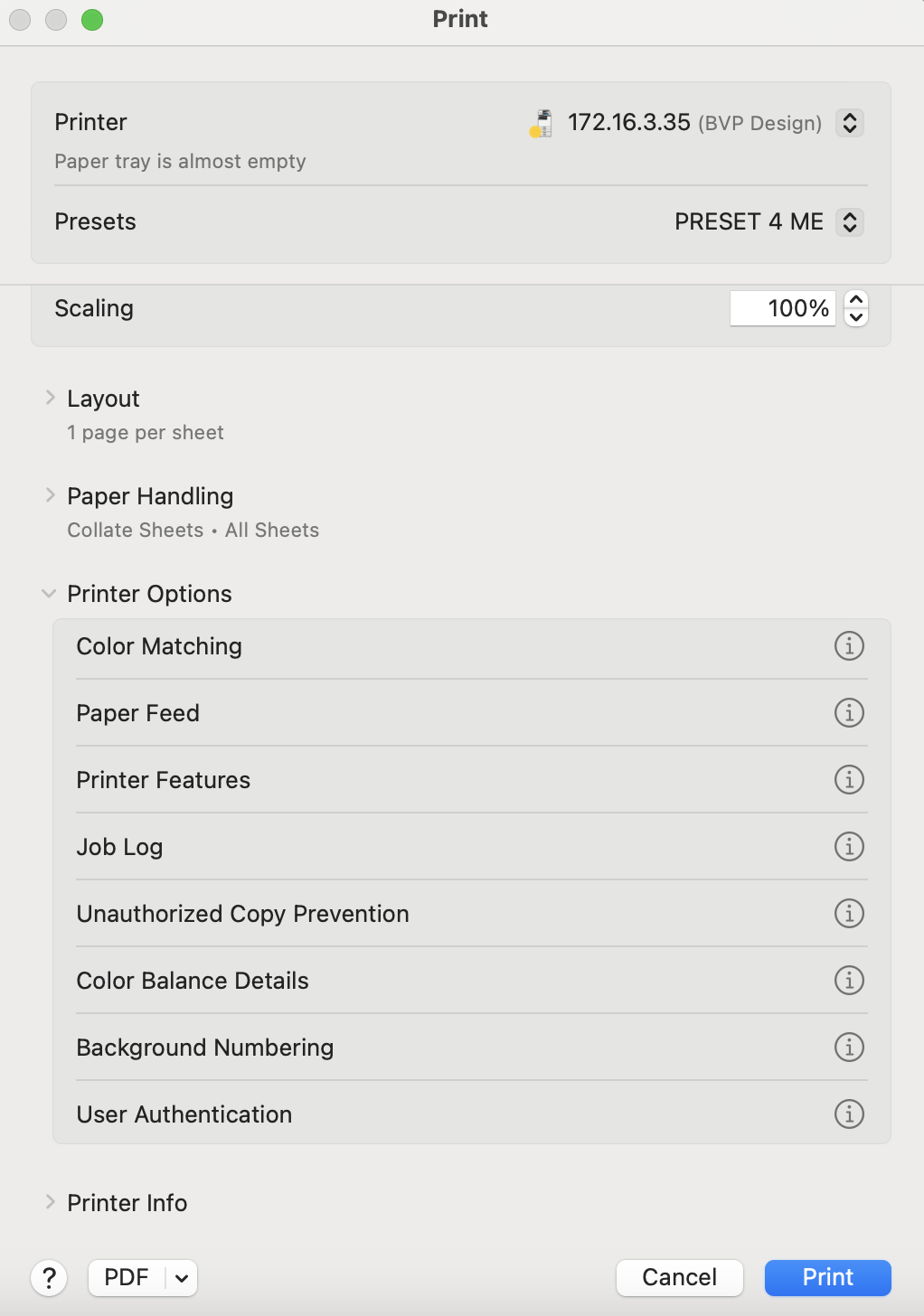
Open a document or browser and select "File>Print"
When the print dialogue pops-up, open "Job Log" and use appropriate settings as below.
Then setup a new preset for locked print (in example below; "PRESET 4 ME"):
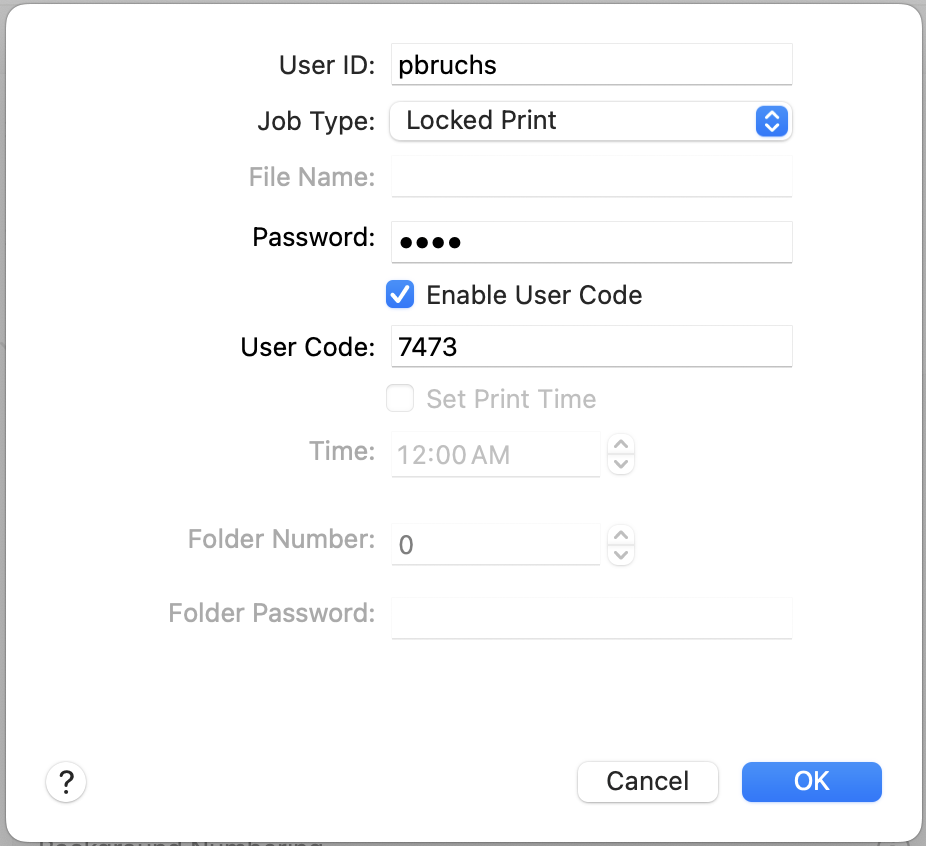
NOTE: The Password AND User Code (below) are the actual "User Code" numbers in the Ricoh Address List. They are both the same. FOR GTC USER NAMES GREATER THAN 8 CHARACTERS, JUST USE THE FIRST EIGHT…IT SHOULD STILL WORK FINE (THE CURRENT RICOH DRIVER ONLY ACCEPTS 8 CHARACTERS - 24AUG21 DOWNLOAD).
MACBOOK PRO RED DOT ISSUE RESOLUTION:
NOTE! RUN THIS SUDO COMMAND AFTER EVERY SYSTEM UPDATE!
You may want to try altering the password interval for the AD bind. To do this, run this command on a bound and properly authenticating Mac:
sudo dsconfigad -passinterval 0
There has been a long standing issue with the default 14 day reset of the device password. Basically, a bound Mac will automatically refresh its random device password with the domain every 14 days (nearly to the second, provided the device is active). Ah, but the order or operations on the Mac appears to be (1) trigger a reset of the device password, (2) write it to the local drive, and then (3) attempt to send the updated password to the DC.
A problem occurs when the DC for what ever reason does not receive the new password. Now the bind configuration on the Mac does not match the computer record in the DC and the bind is not trusted. All future attempts are denied resulting in a failure to communicate with the DC for authentication. By setting the -passinterval to 0, you are telling the Mac never to refresh the bind password.
This is a huge issue with laptops as it is easy to predict that many of the devices may not be in contact with the DC when the 14 day timer expires. This will result in the device being untrusted when it returns to the LAN.
Also, this will have a side effect if you have observant domain admins. Searching AD for Mac records may reveal what appears to be stale records. If you are using automation to remove stale device records or if you have an admin who periodically "cleans house," inform the coworker to leave the Mac records alone. I usually guide clients to create a custom path on the DC for Mac device records. This dedicated OU allows us to isolate the Mac records and exclude them from any unwanted purges.
Having the devices hardwired is a good step as it reduces a lot of the variables associated with the mobility of laptops. But, as celliot147 stated, traditional binds are/have been out of favor with Apple for some time. Take a look at this from 2020 https://www.apple.com/tr/business/docs/site/Kerberos_Single_Sign_on_Extension_User_Guide.pdf
to get started. Note, I assume you have an MDM in place.
From <https://discussions.apple.com/thread/254385731?sortBy=best>




